One of the toughest problems you will ever face as a website owner is getting your website hacked. I have no concerns. The positive news is that it is recoverable on the website. And in this post, we’ll help you take the appropriate measures to delete the “This link could be compromised” warning from Google.
TL;DR
You should instal our WordPress Malware Removal Plugin (MalCare) if you have malware and are trying to only clean up the infection and patch the web. It is going to scrub the site immediately. But to have the “this link could be compromised” message deleted, you’ll need to return and read the rest of the post.
1. Why is Google claiming this site could have been hacked?
Google, as the world’s largest search engine site, takes steps to provide its customers with a stable web interface. It crawls hundreds of thousands of every day websites, many of which turn out to be tainted with malware. It’s fair to say that as hackers find their way into your website they can exploit it. They will use the website to market counterfeit drugs or divert traffic to their website. Your hacked website could hurt visitors in this way.
Google. label your website as hacked to prevent Google search engine users from being victims of such malicious activities and you will have to delete Google blacklist alert(see the image below).
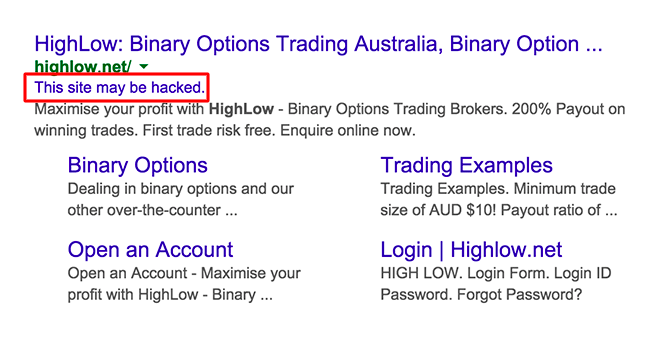
If you find this message on Google’s search page below the name of your website, then your website is most likely to be compromised. In the next segment we’ll show you how this site can be compromised to delete the Google alert.
2. How to Delete “This Link Could Be Compromised” Alert from Google
You need to take two steps to repair the website and they are:
- Remove malware from your website
- Request a review by Google
In the next sections we will address all of these measures in depth. Remember that if your website has been identified as compromised by Google, there’s a fair possibility that other search engines would mark your site as compromised too. The next steps you’ll take will help you to delete the compromised message from every search engine.
Removing Malware
Your website has two main methods to eliminating malware. To get the job done quickly and efficiently, you can use a protection plugin, or you can do it yourself but it needs technological expertise.
Moving forward we will teach you how to use a security plugin to delete malware. But if you’re wondering how manual cleaning works, take a step-by – step look at this guide on how to patch hacked WordPress website.
How to Select a Security Plugin?
The WordPress malware removal plugin first has to decide what kinds of malware are present on your website and where before deleting malware. Not every protection plug-in that you come across will do that.
Some plugins perform a surface-level search, and what this means is that they look at files and directories where malware is contained in general. Since they stop looking anywhere, a whole lot of malware inevitably goes undetected (take WP-VCD malware for example).
Another factor you need to be vigilant when picking a security plug-in is that they are not searching for new malware. That means they’ve got a list of known malware and they’re just going to look for those. And in the process, they end up missing new malware forms that are much harmer to your website. Yet those shortfalls don’t plague the MalCare Surveillance Department.
MalCare will check a website regularly for ransomware. The plugin maintains a list of all modifications and is extensively checked upon discovering some suspicious alteration. That’s how it finds malware in places other plugins usually don’t search for.
Not just that, the plugin goes beyond finding proven malware and probes to find new malware in the design and action of the codes.
Removing Malware With MalCare
All you need to do to clean up your website with MalCare is enable the protection plugin and link your website to the MalCare dashboard. It will immediately start searching the entire web site. If the scanning process is complete you can continue by clicking the Auto-Clean button to clean your website.

MalCare will take a few minutes to clean up the website and once finished, we will continue to the next step.
Submit Website for review
The “This site could be compromised” alert will not be deleted until you tell Google to update the page. Register or log into the Google Search Console to notify Google. Then move to the Security Problems section from your scan console account, and pick Request a Check. You may have to wait a few hours to get Google to delete the alert for up to a few days.
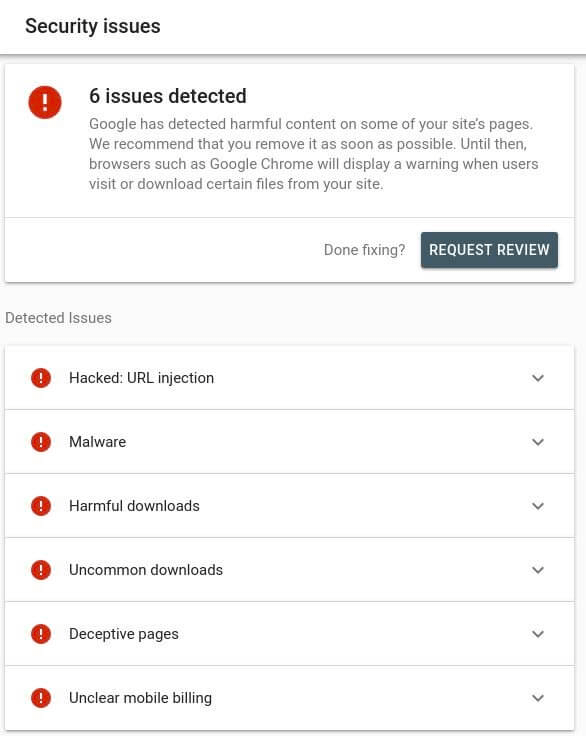
3. How to Prevent Being Suspended in the Future?
Although the problem at hand might have been resolved, there’s no guarantee you won’t be compromised again. You can do a lot, as a WordPress web developer, to enhance the site’s security posture. By taking proactive action, you will escape the scenario. This will mean the website is safe from malware, bots and the rest.
Keep you posted on the Website
We’ve spoken earlier about how skipping updates is a huge reason why websites get hacked. We will recommend that you set aside some time per week to update your website. Look at this detailed article on WordPress alerts to read more about the alerts.
Using more strong credentials
The WordPress login tab is the Website’s most insecure tab. Hackers hack the page and attempt to guess the passwords and usernames. It makes all the difference to have a good password and a special username. And as a website administrator, it’s your duty to use good credentials from all of your website users. It also helps deter assaults by brute force. Therefore you need a good security policy in place.
Install a Security Plugin
Using a protection plugin is the easiest way to guarantee that 247 is safe for your website. The protection plugin performs a regular check on your website and cleanse if it is malware-infected. Most security plugins provide firewalls to help foil attacks that have been initiated on your site. Protection plugin like MalCare provides specialised steps that aim to harden the website against attempts to hack.
With that, you have come to the conclusion of an alert on how to repair “This Site Could Be Compromised.”
It’s worth noting that compromised websites will face other problems such as removal of the web host and blacklisting by Google. We firmly recommend you figure out how these problems are being dealt with by your company and continue to repair them.
Present Impression
Removing the “warning the site could be compromised” requires three key courses of action:
- Clean up your compromised account
- Take preventive steps
- And then, ask Google for a summary
Removal of ransomware means the website no longer poses a threat to users of Google. The best approach that security experts suggest is to add a security plugin to shield the site from potential hack attempts.















Leave a Reply