Privileged users typically hold crucial positions within organizations. They typically have elevated levels of access, authority, and permissions in the organization’s IT systems, networks, applications, and critical data. That’s why they may pose risks to your corporate cybersecurity and monitoring privileged users is paramount.
Moreover, numerous regulations and data security standards, including GDPR, HIPAA, and NIST 800-53, demand organizations monitor privileged users on an official basis. In the following article, we reveal the best practices for Privileged User Monitoring (PUM) that can help you safeguard your critical assets and mitigate cybersecurity threats.
Why PUM is essential?
Within an organization, employees can be divided into two groups depending on their access rights: privileged users and regular users.
While both categories require thorough monitoring, the reasons for that differ:
Regular users are monitored for:
- Evaluating employee performance.
- Enhancing productivity.
- Safeguarding sensitive data and critical systems.
- Mitigating insider and outsider threats.
- Ensuring compliance adherence.
In contrast, privileged users, are watched for:
- Checking how they handle sensitive data.
- Tracking modifications within systems.
- Identifying authorized access.
- Safeguarding sensitive data and critical systems.
- Mitigating insider and outsider threats.
- Ensuring compliance adherence.

From all this, it’s easy to conclude that whereas regular users are typically monitored to evaluate their performance, privileged users are watched to make sure they don’t misuse their privileges.
Now, you may ask, “How to monitor privileged accounts effectively?”. Let’s take a look at the 10 best practices for privileged activity monitoring.
10 best practices for privileged user monitoring
We’ve narrowed down the best practices for PUM that can help you maintain the integrity and confidentiality of critical systems and data within your organization.
1. Completely monitor privileged user actions
Many organizations only keep an eye on actions with specific types of data. But it’s a big mistake.
Since privileged users often have almost unlimited access to your critical assets, it’s crucial to pay attention to their every action.
Choose a user activity monitoring solution that records information in light formats while still capturing every user action on screenshots or video recordings. The ability to look through these records later will be a big advantage, especially if an incident occurs.
2. Restrict privileges
The fewer privileged users you have and the fewer privileges they have, the easier it will be to monitor all of their actions. That’s why, consider giving elevated access rights only to the employees who really need that, only for a limited time.
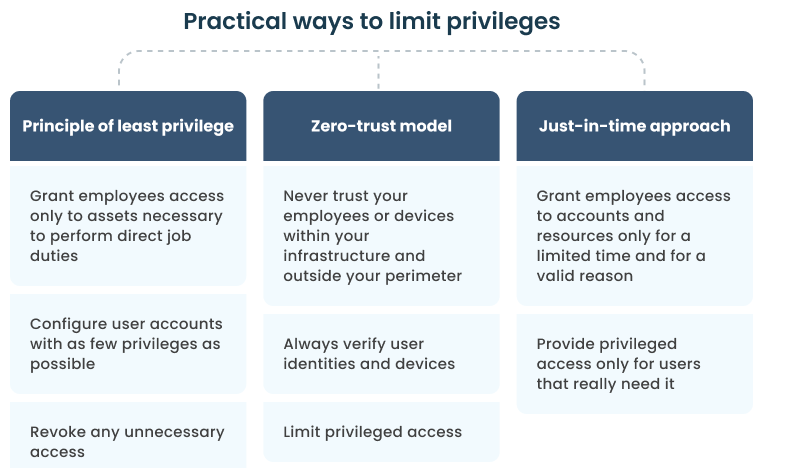
To limit user privileges, you may follow the principle of least privilege, a zero trust architecture, or just-in-time PAM.
3. Get a clear view of all admin accounts
It’s a common practice when privileged users share their access rights with others. For example, some users may have admin-like access permissions but aren’t part of the admin groups, like domain admins. They are called shadow admins, and they are rather tricky to monitor.
The 2023 Insider Threat Report by Gurucul revealed that 54% of insiders had credentialed access to networks and services. Therefore, it’s crucial to monitor shadow admins as well. You should not only watch what they do within your corporate network but also detect when new accounts are created or old ones are removed.
4. Watch USB devices in your network
A malicious insider may use a USB drive to steal important data. Therefore, you should watch all USB devices connected to your network to keep your organization’s data safe, especially the USB devices used by privileged users.
It’s essential to integrate monitoring software that wil be able to track USB device connections, send alerts when unusual USB devices are detected, and block them if need be.
5. Implement secondary authentication for shared accounts
Many organizations opt for shared privileged accounts in order to streamline their administrative processes. However, this inadvertently opens the door to cybersecurity vulnerabilities within their IT networks.
Shared accounts complicate user activity monitoring and auditing since they make it nearly impossible to differentiate users’ actions. By implementing secondary user authentication as an added security measure, you can effectively identify the activities of privileged users who share accounts.
6. Keep an eye on remote connections
With an increasing number of remote employees, security threats become more acute. Organizations grant remote access to their data not only to regular employees but also to part-time workers and subcontractors. If such users access sensitive information in your network, consider using remote desktop monitoring software to keep a close eye on them.
For privileged users, you should also take care of RDP monitoring (Remote Desktop Protocol sessions). RDP sessions can be exploited by malicious insiders to gain unauthorized access to sensitive data or perform unauthorized actions within the network. RDP session recording and monitoring help identify suspicious activities and prevent insider threats. Also, we highly recommend you specify which systems and data can be accessed through remote logins and create whitelists for IP or MAC addresses.
7. Prevent logs from being modified.
Depending on the extent of their permissions, privileged users might have the ability to modify or even delete logs and records. To address this issue, we advise you to grant full access to system logs exclusively to a specific role or a restricted group of users.
When selecting monitoring software, it’s crucial to opt for a solution that prevents any alterations to logs or reports. By using such software, you can have a piece of mind, knowing that records remain unaltered.
8. Watch for unusual behavior
The actions of an external attacker or a malicious insider may differ from those of an authorized user.

User and Entity Behavior Analytics (UEBA) technology can identify anomalous activity among users within your corporate network. UEBA tools can help you quickly detect unusual activities of privileged users.
9. Conduct cybersecurity training among your employees
Employees lacking adequate cybersecurity knowledge might not grasp the importance of being monitored, and could potentially attempt to deceive your security measures and policies.
Elevating the level of cybersecurity awareness among your employees is critical. Your employees will be able to identify suspicious actions and promptly notify the security team.
10. Continuously monitor privileged users
Conducting user activity monitoring at intervals doesn’t guarantee comprehensive insight into a user’s actions and, thus, effective protection of your sensitive data.
Privileged user monitoring is an ongoing process that requires continuous monitroing. It’s vital to regularly review your privileged user monitoring procedures and constantly enhance them with the best PUM practices.
How can Ekran System help?
Ekran System is a full-cycle insider risk management platform, enabling you to monitor of all types of users, including those with elevated access. It also helps you manage access to critical systems, applications, and data within your network.
With Ekran System, you can implement the best PUM practices thanks to a rich set of features for managing insider threats:
- Continuous employee monitoring across all servers (including jump servers, endpoints, and remote workstations).
- Privileged user monitoring and managing privileged access for your employees and third parties.
- Windows monitoring to record both local and RDP user sessions.
- Recording of context-rich user sessions (local, terminal, SSH, and RDP) in a searchable video format.
- Collecting metadata on user activities, such as application names, visited URLs, and typed keystrokes.
- Alerting and responding to cybersecurity incidents through user blocking and process termination.
- Monitoring connected USB devices, including flash drives and USB modems.
- Generating detailed reports and exporting user session data to facilitate forensic investigations.
These features can help you get a full visibility into privileged user accounts and the assets they can access. Furthermore, the functionality of Ekran System can help you meet such cybersecurity standards as SOX, HIPAA, PCI DSS, and many others.
Final thoughts
As insider threats and data breaches are becoming increasingly common among organizations of all sizes, implementing effective strategies for privileged user monitoring becomes essential. By monitoring privileged users, you’ll be able to minimize insider threats and prevent your sensitive data from breach.
The ten practices listed above can help you create an effective privileged user management system. And Ekran System can help you get full visibility into privileged accounts, users, and third-party vendors within your corporate network. Importantly, Ekran System offers robust capabilities for monitoring RPD connections, ensuring a higher level of security.














